Security defenses that rely heavily on passwords are no longer enough to safeguard us. In fact, they are leaving us more vulnerable to attacks. Cybercriminals have started using sophisticated techniques and technologies to guess, extract, and replicate your identity codes. Alarming! Isn’t it?
Then what is the solution? How do we address this vulnerability?
The ideal solution for both people and organizations would be an element that is nearly impossible to replicate – Biometrics.
‘Everyone is unique in their own way.’ This statement applies to human biology as well.
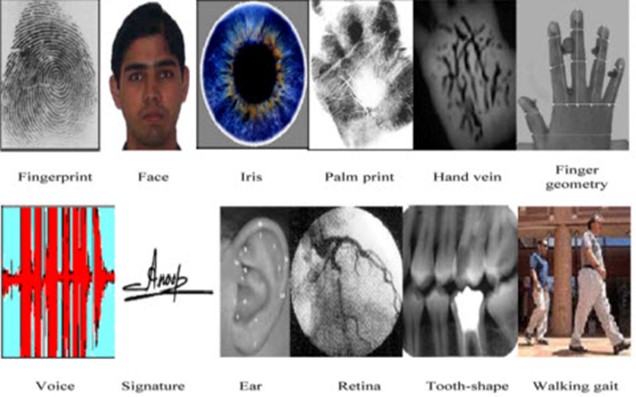
It is a known fact that we all have different physical features and behavioral traits. They are so diverse and complex that it is almost impossible to replicate every biological component that makes us unique. Hence, our fingerprints, facial features, iris patterns, etc, are leveraged to create a defense mechanism that can thwart cyberattacks effortlessly.
These inherent advantages make biometric authentication a rising star in Identity and Access Management (IAM).
Latest Trends in Biometrics
- Multimodal Biometrics:
In the digital world, achieving ‘complete safety’ is a myth. Though adding a biometric element boots protection, we can never underestimate the level to which cybercriminals go to crack the defense system. Hence, we constantly need to upgrade our defenses.
One such upgrade is multimodal biometrics. As the name suggests, this technique combines multiple biometrics for cyber protection. For instance, you can use both fingerprint and facial recognition as factors for authentication. Similarly, iris scans, voice recognition, etc, can be added to enhance the overall security posture of the individual.

2. Continuous Authentication:
Traditional biometric authentication happens at a single point, for instance, when you unlock your phone. On the other hand, continuous authentication analyzes behavior patterns like type speed, mouse movements, etc, throughout the interaction with your phone or system. Even if a cybercriminal successfully replicates one biometric, behavioral anomalies can be easily detected, alerting you to take the next step.

3. Behavioral Biometrics:There are two aspects to biometrics – physical features and behavioral patterns. Behavioral patterns include gait (the way a person walks or moves their limbs while walking), keystroke dynamics (typing patterns), etc. Even how you sign your name on the touch screen can provide unique identifiers for authentication. They are still in the early stages of exploration but have the potential to create a more secure workspace and verification process.

4. On-device Biometrics:
On-device biometrics involves storing and processing biometric data directly on devices like smartphones and wearables instead of relying on centralized servers. This method improves both privacy and security. Moreover, features like offline authentication are an added advantage, especially when the internet connectivity is limited.

5. Liveness Detection:
Spoofing biometric data is difficult, but rising technologies like deepfakes can make it vulnerable. Hence, liveness detection techniques like analyzing blood flow, capturing subtle eye movements, etc., are being explored as effective alternatives to check if the person seeking authentication is alive and present.

Biometric Authentication
Enhanced Security:
Stronger Authentication
Multi-factor Authentication (MFA)
Continuous Authentication
Improved User Experience:
Convenience
Touchless Authentication
Enhanced Personalization
Conclusion:
Overall, the rise of biometric authentication is a sign that the digital world is shifting toward a more robust and user-friendly access control system. By replacing traditional authentication factors like passwords with unique physical or behavioral traits, we can achieve both protection and convenience, making the interconnected world a more confident space to explore opportunities.