In today’s digitally connected era, where data holds immense value and information moves swiftly, organizations navigate the ongoing challenge of protecting their digital assets from cyber threats. Despite significant investments in security, it’s vital to understand that employees’ watchful minds serve as the primary line of defense.
Employee awareness training is no longer another checkbox exercise but a significant cybersecurity measure that helps create a strong line of defense against internal and external threats.
The Crucial Role of Employee Awareness Training
Employees, often the weakest link in security, may unknowingly open doors to cyber threats. Clicking on suspicious links or falling for scams can expose the organization. Mitigating this risk is crucial, and employee awareness training is the key. Employee awareness training emerges as the linchpin for mitigating this risk.
Human Factor Vulnerability: Equip Employees with Awareness Training to Defend Against Phishing, Malware, and Social Engineering Threats.
Evolving Threat Landscape: Crucial Employee Knowledge for Recognizing and Reporting Emerging Cyber Threats Effectively.
Compliance Mandates: Ensure Adherence to Data Security Regulations with Mandatory Employee Awareness Training.
Data Breach Mitigation: Significantly Reduce Risks with Training on Data Security Best Practices and Mitigate Potential Breaches.
Competitive Trust Advantage: Build a Competitive Edge by Showcasing a Strong Cybersecurity Culture Through Awareness Training.
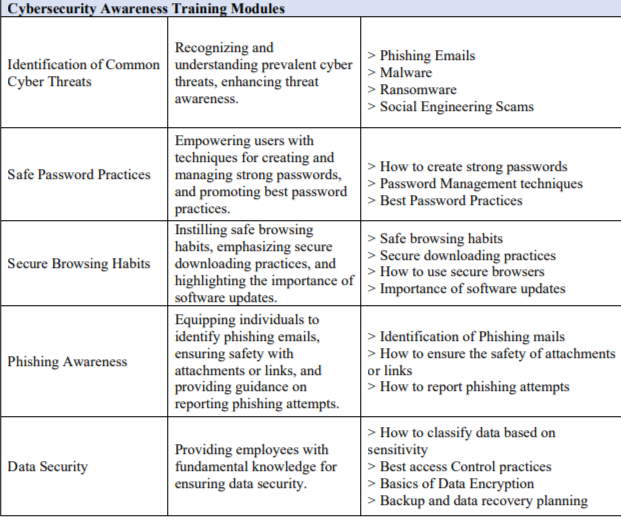
Key Areas to be Covered in Employee Awareness Training
Benefits of Investing in Employee Awareness Training
Reduced Risk of Cyberattacks: Educated employees become formidable barriers, making it
challenging for attackers to compromise organizational systems.
Improved Data Security: Employees cognizant of the significance of data security are more
likely to proactively contribute to its protection.
Increased Compliance: Certain industry regulations mandate employee awareness training on
cybersecurity, ensuring organizational adherence.
Enhanced Brand Reputation: Successful avoidance of data breaches contributes significantly to
maintaining a positive brand image.
How to Cultivate a Resilient Cybersecurity Culture?
- Simulation is Preparation: Don’t let the first attack be your training ground. Conduct simulated
phishing attacks and security awareness campaigns to test your employees’ vigilance and identify
areas for improvement. Practice makes perfect, even in the realm of cybersecurity. - Make it Engaging, Not Daunting: Ditch the boring lectures and one-size-fits-all approach.
Instead, employ interactive training modules, gamified quizzes, and real-life scenarios to keep
employees engaged. Remember, learning should be fun, not a chore. - Foster Open Communication: Create a culture where employees feel comfortable reporting
suspicious activity or breaches without fear of judgment or consequences. Encourage open
communication between all levels of your organization and promote a collaborative approach to
cybersecurity. - Lead by Example: Remember, security starts at the top. Executives and leadership must
actively participate in training and demonstrate strong cybersecurity practices. Actions speak
louder than words, especially when it comes to setting the tone for security awareness. - Continuous Improvement: Don’t consider training a one-time event. Make it an ongoing
process with regular updates, reminders, and reinforcement sessions. - Reward Good Behavior: Recognizing and rewarding employees who consistently adhere to
cybersecurity practices reinforce the desired culture.
Conclusion:
As you actively shape a robust cybersecurity culture, your organization strategically invests in
defending against the ever-evolving cyber threat. This ongoing commitment, supported by
effective employee awareness training, equips your business not only to confront but to
successfully navigate the intricate challenges presented by cyber threats





